IoT Remote SSH: Easy & Secure Access [Free Download Guide]
Is gaining complete, secure dominion over your IoT devices from anywhere on the globe merely a pipe dream? It's absolutely within reach, and it's more critical now than ever before, especially as the digital landscape expands and vulnerabilities increase.
The Internet of Things (IoT) has exploded, and with it, the necessity for robust, secure remote access solutions. Imagine the power of managing your Raspberry Pi, updating software, monitoring performance, and troubleshooting issues from thousands of miles away, all without physically touching the device. This level of control and flexibility is no longer a luxury; it's a necessity for both hobbyists and seasoned professionals navigating the complex world of connected devices. The key to unlocking this potential lies in leveraging Secure Shell (SSH) over the internet, but doing so safely and efficiently requires understanding the landscape of available tools and techniques. It demands a solution that cuts through the complexities of IP discovery, firewall configurations, and potential security vulnerabilities.
| Aspect | Details |
|---|---|
| Concept | IoT Remote SSH |
| Definition | Securely accessing and managing IoT devices from a remote location using SSH. |
| Key Benefits | Remote management, secure connection, bypassing firewall restrictions, simplified access. |
| Security Measures | Data encryption via SSH tunnel, system user or SSH key-based authentication. |
| Typical Tools | PuTTY (for Windows), Terminal (for macOS/Linux), SocketXP, Remote.it |
| Challenges | Initial setup complexity, ensuring robust security, potential latency issues. |
| Use Cases | Remote monitoring, software updates, troubleshooting, data collection. |
| Alternative Solutions | VPNs, cloud-based IoT platforms |
| Website | Raspberry Pi Foundation |
Many search for a magic bullet: "IoT remote SSH over internet free download." The reality is that while free tools exist, security and ease of use often come at a premium. The phrase itself highlights a common pain point: the desire for a simple, cost-effective way to gain remote access without the headaches of traditional network configuration. The search results, often returning with "We did not find results for:" or "Check spelling or type a new query," underscore the challenge of finding a perfectly tailored solution. But don't despair; the answer lies in understanding the underlying principles and selecting the right tools for your specific needs.
- Victor Reynolds Train Accident The Viral Video Aftermath
- Reptile Radiator Guard Guide Habistat Prorep Find It Here
One of the most significant hurdles is the need to discover the IoT device's IP address and navigate the often-treacherous waters of firewall settings. Opening ports and configuring dynamic DNS can be daunting, especially for those new to network administration. This complexity can be a major barrier to entry, preventing users from fully leveraging the potential of their IoT devices. However, innovative solutions are emerging that bypass these traditional requirements, offering a more streamlined and user-friendly experience.
The good news is that it is no longer necessary to wrestle with port forwarding or expose your devices directly to the public internet. Solutions like SocketXP and Remote.it provide secure tunnels that eliminate the need to fiddle with firewall settings. All data transmitted through these tunnels is wrapped in encrypted SSH, ensuring confidentiality and integrity. This means your sensitive information is protected from eavesdropping and unauthorized access, providing peace of mind in an increasingly connected world.
The power of SSH lies in its ability to establish a secure, encrypted connection between your client machine and the IoT device. Whether you prefer using the system user or SSH key-based secure authentication, the process remains robust and reliable. Standard client tools like PuTTY (for Windows) and the built-in terminal on macOS and Linux provide familiar interfaces for interacting with your devices. This eliminates the need to learn new and complicated software, allowing you to focus on the task at hand.
- Future Of Iob Internet Of Bodies Tech Breakthroughs
- Somali Wasmo Telegram Channels Find The Best Join Now
The convergence of IoT and secure remote access has brought solutions like remote IoT web SSH for Raspberry Pi into sharp focus. These platforms offer unprecedented control and flexibility, empowering users of all skill levels to manage their devices with ease. By encrypting data between the client and server, SSH helps to preserve data integrity and shield devices from unauthorized access. This is particularly crucial in environments where sensitive data is being collected and transmitted.
The process of establishing remote SSH access to an IoT device over the internet involves several key steps. First and foremost, an SSH server must be running and properly configured on the IoT device itself. This server acts as the gateway, listening for incoming connection requests and authenticating users. Once the server is configured, you can use a client application (like PuTTY or the terminal) to initiate the connection. However, without a solution that bypasses traditional network configurations, you would need to know the device's public IP address and ensure that the firewall is configured to allow SSH traffic on port 22 (or a custom port you have configured). This is where solutions like SocketXP and Remote.it come into play, simplifying the process and enhancing security.
To illustrate the process, consider using SocketXP to gain remote SSH access to your IoT device. The first step is to download and install the SocketXP IoT agent on your device. This agent acts as a secure tunnel, creating an outbound connection to the SocketXP servers. Once the agent is installed and running, you can use the SocketXP client on your local machine to establish an SSH connection to your device through the secure tunnel. This eliminates the need to expose your device directly to the internet or configure complex firewall rules.
Platforms like Remote.it also offer a robust solution for managing remote IoT devices and servers securely. These platforms provide a user-friendly interface for connecting to your devices, regardless of their location or network configuration. By leveraging secure tunnels and encryption, they ensure that your data is protected from unauthorized access.
With the rapid rise of IoT technology, the need for secure and efficient remote management systems has never been greater. Whether you are a hobbyist tinkering with a Raspberry Pi or a professional managing a fleet of IoT devices, understanding the principles of remote SSH and leveraging the right tools can unlock a world of possibilities. By prioritizing security, simplicity, and ease of use, you can ensure that your IoT devices are accessible, manageable, and protected from the ever-evolving threats of the digital world.
Furthermore, beyond the basic setup and security considerations, optimizing the performance of your remote SSH connection is paramount. Network latency, bandwidth limitations, and device processing power can all impact the responsiveness of your connection. To mitigate these issues, consider using lightweight SSH clients, optimizing your SSH configuration for speed, and minimizing the amount of data transmitted over the connection. Compressing data before transmission can also significantly improve performance, especially in environments with limited bandwidth.
Another critical aspect of remote IoT SSH is the management of user access and permissions. It's crucial to implement a robust authentication system to prevent unauthorized access to your devices. SSH key-based authentication is generally considered more secure than password-based authentication, as it eliminates the risk of password cracking. By generating a unique SSH key pair for each user and carefully managing access permissions, you can significantly reduce the risk of security breaches.
Regularly updating your SSH server software and the operating system on your IoT device is also essential for maintaining security. Software updates often include patches for known vulnerabilities, which can be exploited by attackers if left unaddressed. By staying up-to-date with the latest security patches, you can minimize the risk of your devices being compromised.
In addition to these technical considerations, it's important to establish clear security policies and procedures for managing your IoT devices. This includes defining roles and responsibilities for users, implementing strong password policies, and regularly auditing access logs to detect suspicious activity. By taking a proactive approach to security, you can minimize the risk of security incidents and protect your data from unauthorized access.
The future of remote IoT SSH is likely to be shaped by several key trends. One trend is the increasing adoption of cloud-based IoT platforms, which offer centralized management and security features. These platforms provide a single pane of glass for managing all of your IoT devices, simplifying the process of remote access and security monitoring. Another trend is the development of more sophisticated security tools, such as intrusion detection systems and vulnerability scanners, which can help to identify and mitigate potential security threats.
As IoT technology continues to evolve, remote SSH will remain a critical tool for managing and securing connected devices. By understanding the underlying principles, leveraging the right tools, and implementing robust security measures, you can unlock the full potential of IoT and ensure that your devices are accessible, manageable, and protected from the ever-evolving threats of the digital world.
The challenge often lies not just in establishing a connection, but in maintaining a reliable and secure connection over extended periods. Intermittent network connectivity, power outages, and software glitches can all disrupt your remote SSH session. To mitigate these issues, consider implementing a watchdog timer on your IoT device, which can automatically reboot the device if it becomes unresponsive. You can also use a monitoring service to track the health and status of your devices, alerting you to any potential problems before they escalate.
Another factor to consider is the impact of network address translation (NAT) on remote SSH connections. NAT is a technique used by routers to translate private IP addresses to public IP addresses, allowing multiple devices on a local network to share a single internet connection. However, NAT can also complicate the process of establishing remote SSH connections, as it can prevent incoming connections from reaching your IoT device. To overcome this issue, you can use port forwarding or a VPN to create a direct connection between your client machine and your IoT device.
In addition to security and reliability, ease of use is also a critical factor to consider when choosing a remote SSH solution. Many users, particularly those new to IoT, may find the command-line interface of traditional SSH clients intimidating. Fortunately, there are several graphical SSH clients available that provide a more user-friendly experience. These clients offer features such as drag-and-drop file transfer, session management, and integrated terminal emulators, making it easier to manage your IoT devices remotely.
The selection of the appropriate hardware also influences the efficiency of remote IoT SSH operations. While Raspberry Pi devices are a popular choice due to their versatility and affordability, other options exist. Selecting a device with sufficient processing power and memory is crucial for ensuring smooth operation, especially when running resource-intensive applications. Furthermore, the choice of operating system can also have a significant impact on performance. Lightweight operating systems, such as Alpine Linux, can minimize resource consumption and improve responsiveness.
Beyond the core functionality of remote SSH, there are several advanced techniques that can further enhance your IoT management capabilities. One such technique is the use of SSH tunneling to create secure tunnels for other network protocols. For example, you can use SSH tunneling to encrypt VNC traffic, allowing you to remotely control the graphical user interface of your IoT device securely. You can also use SSH tunneling to forward ports, allowing you to access services running on your IoT device from your local machine.
Another advanced technique is the use of SSH multiplexing, which allows you to establish multiple SSH sessions over a single TCP connection. This can significantly improve performance, especially in environments with high latency. SSH multiplexing reduces the overhead associated with establishing multiple TCP connections, resulting in faster response times and improved overall throughput.
The legal and ethical considerations surrounding remote IoT SSH are also important to address. It is crucial to ensure that you have the necessary permissions to access and manage your IoT devices remotely. Unauthorized access to IoT devices can have serious legal consequences, including fines and imprisonment. It is also important to respect the privacy of others when accessing and managing IoT devices remotely. Avoid accessing or collecting data that you are not authorized to access, and always comply with applicable privacy laws and regulations.
The integration of remote IoT SSH with other technologies, such as cloud computing and artificial intelligence, is opening up new possibilities for IoT applications. Cloud computing provides a scalable and cost-effective platform for storing and processing the data collected by IoT devices. Artificial intelligence can be used to analyze this data and identify patterns and insights that can be used to improve the performance and efficiency of IoT systems.
As IoT technology continues to mature, remote SSH will play an increasingly important role in enabling the remote management and security of connected devices. By embracing the latest tools and techniques, and by adhering to best practices for security and privacy, you can unlock the full potential of IoT and create innovative solutions that improve our lives and transform our world.
Looking ahead, the evolution of remote IoT SSH is inextricably linked to advancements in network technologies, particularly the rollout of 5G and the proliferation of low-power wide-area networks (LPWANs). 5G offers significantly higher bandwidth and lower latency compared to previous generations of mobile networks, enabling faster and more responsive remote SSH connections. LPWANs, such as LoRaWAN and NB-IoT, are designed for low-bandwidth, long-range communication, making them ideal for connecting IoT devices in remote or challenging environments. These technologies will enable new and innovative IoT applications that require reliable and secure remote access.
The development of more secure and efficient authentication methods is also a key area of focus. Biometric authentication, such as fingerprint scanning and facial recognition, offers a more secure alternative to traditional password-based authentication. Multi-factor authentication (MFA), which requires users to provide multiple forms of identification, adds an additional layer of security, making it more difficult for attackers to gain unauthorized access. These advancements will further enhance the security of remote IoT SSH connections.
The increasing use of containerization technologies, such as Docker and Kubernetes, is also transforming the landscape of IoT development and deployment. Containerization allows developers to package applications and their dependencies into isolated containers, making it easier to deploy and manage applications on IoT devices. Remote SSH can be used to manage and monitor these containers remotely, providing a convenient and efficient way to update and maintain IoT applications.
The rise of edge computing is another trend that is impacting the evolution of remote IoT SSH. Edge computing involves processing data closer to the source, reducing the need to transmit large amounts of data to the cloud. This can significantly improve performance and reduce latency, making it ideal for applications that require real-time processing. Remote SSH can be used to manage and monitor edge devices remotely, enabling organizations to deploy and manage distributed IoT systems more effectively.
The development of more user-friendly and intuitive remote SSH tools is also crucial for broadening the adoption of IoT technology. Many users, particularly those with limited technical expertise, may find the command-line interface of traditional SSH clients intimidating. The development of graphical SSH clients with intuitive user interfaces and automated configuration tools will make it easier for users to manage and monitor their IoT devices remotely.
Finally, the education and training of IoT professionals is essential for ensuring the secure and effective deployment of IoT systems. Organizations need to invest in training programs that teach IoT professionals how to properly configure and secure remote SSH connections. These programs should cover topics such as SSH key management, firewall configuration, intrusion detection, and vulnerability scanning. By investing in education and training, organizations can ensure that their IoT systems are protected from cyber threats.

SSH Client SFTP Terminal and Telnet Free download and install on
How to Connect to a Remote Server Over SSH on Windows Linode Docs
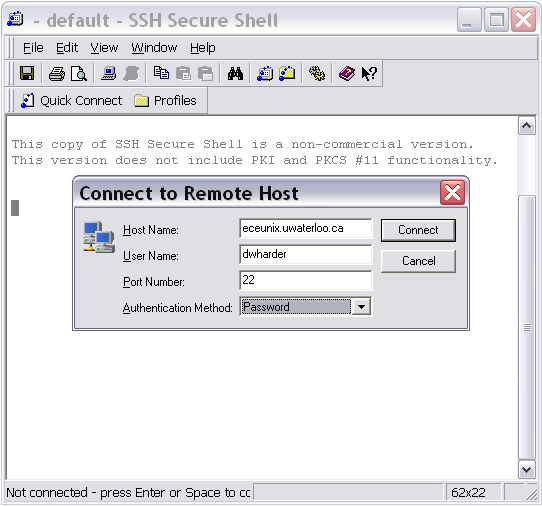
SSH Secure Shell Client MTE 241 University of Waterloo