Remote Access Tips: TeamViewer & Alternatives Explored!
Ever wished you could be in two places at once, or effortlessly assist someone with their tech troubles from miles away? Remote access software is no longer a futuristic fantasy, it's an everyday reality.
In a world increasingly reliant on technology, the ability to remotely access and control devices has become indispensable. Whether it's for providing technical support, collaborating on projects, or simply accessing files from a different location, remote access software offers a powerful solution. But with a plethora of options available, finding the right tool can be overwhelming. This article delves into the landscape of remote access solutions, exploring popular choices, their features, and the specific needs they cater to.
| Information | |
|---|---|
| Name | Remote Access Software Solutions |
| Category | Software |
| Function | Remote access, remote control, and remote support |
| Platforms | Windows, macOS, Android, iOS |
| Key Features | Screen sharing, file transfer, remote printing, wake-on-LAN |
| Use Cases | Technical support, remote work, collaboration, gaming |
| Example Software | TeamViewer, TightVNC, Roku Mobile App |
| Reference | TeamViewer Official Website |
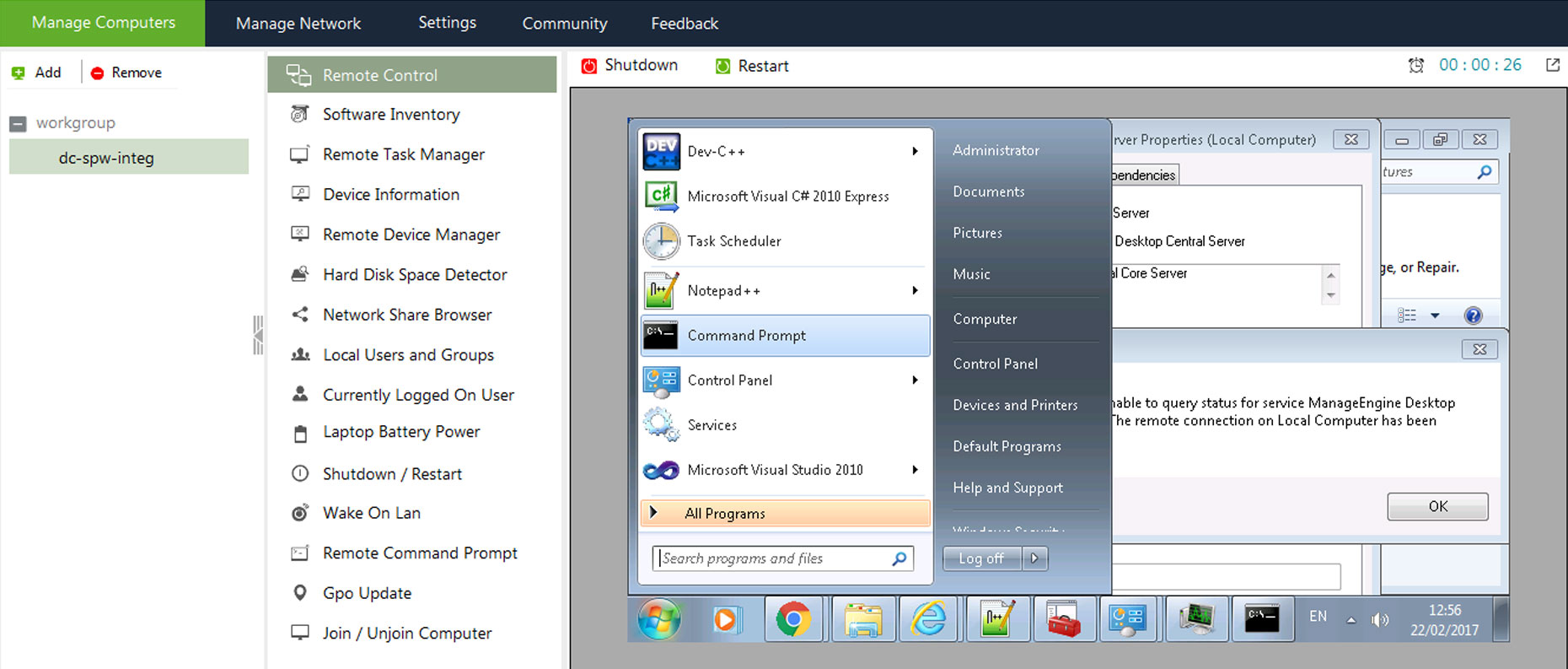
One of the most well-known names in the remote access arena is TeamViewer. This comprehensive solution offers a wide array of features designed to cater to both personal and professional users. Its cross-platform compatibility is a major advantage, allowing you to connect to devices running Windows, macOS, Android, and iOS. TeamViewer facilitates remote support, enabling technicians to troubleshoot issues on a client's computer as if they were physically present. It also supports remote control, allowing users to access and operate computers or mobile devices from anywhere in the world. Furthermore, TeamViewer boasts remote gaming capabilities, allowing users to play PC games remotely on their mobile devices.
- Corinna Jagger The Untold Story Of Mick Jaggers Daughter
- Mitchell Moranis Alles Ber Rick Moranis Sohn
The ease of use is a significant factor contributing to TeamViewer's popularity. Setting up the software is straightforward, and the intuitive interface makes it easy to connect to remote devices. For mobile users, TeamViewer offers dedicated apps for iPhones, iPads, Android phones, and Android tablets. Alternatively, users can access remote devices directly from their web browser via the web client.
Beyond its core remote access functionality, TeamViewer provides a suite of additional features that enhance the user experience. These include file transfer, allowing users to seamlessly move files between their local and remote devices. Screen sharing enables collaboration, allowing multiple users to view the same screen simultaneously. Remote printing makes it possible to print documents from a remote computer on a local printer. Wake-on-LAN functionality allows users to remotely power on computers that are in sleep mode or turned off.
While TeamViewer is a robust and feature-rich solution, it's not the only option available. TightVNC is a free and open-source alternative that offers a more lightweight approach to remote access. Unlike TeamViewer, TightVNC is primarily designed for controlling computers over a network. Its simplicity and open-source nature make it a popular choice for users who prioritize control and customizability.
- No Results Found Tips Spelling Amp Victoryaxos Inspiring Story
- Unblocked Games G Your Gateway To Fun Play Now
TightVNC's interface is straightforward, allowing users to interact with the remote screen as if they were sitting in front of it. While it may not offer the same breadth of features as TeamViewer, it provides a reliable and efficient way to access and control remote computers. Its open-source nature allows developers to customize the software to meet their specific needs.
In addition to TeamViewer and TightVNC, there are other remote access solutions that cater to specific niches. The Roku mobile app, for example, serves as a companion app for Roku streaming devices. It allows users to control their Roku device, browse content, and access additional features that enhance the streaming experience.
The Roku mobile app provides a convenient way to navigate the Roku interface, especially when the physical remote control is not readily available. It also offers features such as voice search, allowing users to quickly find their favorite shows and movies. Furthermore, the app provides access to private listening, enabling users to listen to audio content through headphones connected to their mobile device.
Choosing the right remote access software depends on individual needs and priorities. TeamViewer is a comprehensive solution that offers a wide range of features and cross-platform compatibility, making it suitable for both personal and professional use. TightVNC is a lightweight and open-source alternative that provides a simple and efficient way to control computers over a network. The Roku mobile app caters specifically to Roku streaming device users, offering a convenient way to control their device and access additional features.
The ability to remotely access and control devices has revolutionized the way we interact with technology. Whether it's for providing technical support, collaborating on projects, or simply accessing files from a different location, remote access software offers a powerful and versatile solution. By carefully considering your needs and priorities, you can choose the right tool to unlock the potential of remote access and enhance your digital experience.
The security implications of remote access software are paramount. Any tool that grants control over a device from a remote location inherently carries a risk. It's crucial to understand the security measures employed by each software and to implement best practices to protect your systems. Strong passwords, two-factor authentication, and keeping software updated are all essential. Furthermore, be cautious about granting access to unknown or untrusted parties.
Beyond the popular names, many other remote access solutions cater to specific industries or use cases. For instance, some are designed for IT professionals managing large networks, offering features like centralized management and automated patching. Others are tailored for specific devices, such as point-of-sale systems or industrial equipment. Researching industry-specific solutions can often yield a tool that perfectly fits your unique requirements.
The landscape of remote access is constantly evolving. New technologies, such as WebRTC, are enabling browser-based remote access without the need for dedicated software. Artificial intelligence is being integrated to improve performance and security. As technology advances, expect to see even more innovative and sophisticated remote access solutions emerge.
Consider the level of technical expertise required to set up and use the software. Some solutions are designed for ease of use, with simple interfaces and automated configuration. Others offer more advanced features but require a higher level of technical knowledge. Choose a solution that aligns with your comfort level and technical capabilities.
Many remote access software solutions offer free versions for personal use, while others require a paid subscription. Evaluate the pricing models and features offered at each tier to determine the most cost-effective solution for your needs. Consider factors such as the number of devices you need to access, the frequency of use, and the features you require.
The quality of customer support can be a significant factor, especially if you encounter issues or need assistance with setup or configuration. Check online reviews and forums to gauge the responsiveness and helpfulness of the vendor's customer support team. Consider whether they offer phone, email, or chat support.
Ensure that the remote access software is compatible with your operating system and devices. Some solutions may only support specific platforms or require certain hardware configurations. Check the system requirements before installing the software to avoid compatibility issues.
Remote access software often requires firewall configuration to allow connections to be established. Ensure that you understand the firewall settings required by the software and that you have the necessary permissions to modify your firewall configuration. Incorrect firewall settings can prevent the software from working properly.
Remote access software can consume significant bandwidth, especially when streaming video or transferring large files. Consider your internet connection speed and bandwidth limits when using remote access software. If you have a slow internet connection, you may experience lag or performance issues.
Remote access software can be used for malicious purposes, such as stealing data or installing malware. Be cautious about granting access to unknown or untrusted parties. Only use remote access software with people you trust and verify their identity before granting access. Keep your software updated with the latest security patches to protect against vulnerabilities.
The ability to remotely access and control devices is becoming increasingly essential in today's interconnected world. By understanding the various options available, considering the security implications, and implementing best practices, you can leverage the power of remote access to enhance your productivity, collaboration, and overall digital experience.
Consider the legal and compliance implications of using remote access software, especially in a business setting. Some industries have specific regulations regarding data privacy and security that may impact the use of remote access tools. Ensure that you comply with all applicable laws and regulations.
Document your remote access procedures and policies to ensure consistency and security. Define who is authorized to use remote access software, what devices they can access, and what activities are permitted. Regularly review and update your policies to reflect changes in technology and business needs.
Implement monitoring and auditing procedures to track remote access activity and identify potential security threats. Log all remote access sessions, including the user, device, time, and duration. Regularly review the logs to detect suspicious activity and investigate any anomalies.
Provide training to your employees on the proper use of remote access software and the importance of security. Educate them about the risks of phishing, social engineering, and malware, and how to protect themselves against these threats. Reinforce the importance of following security policies and procedures.
Perform regular security assessments and penetration testing to identify vulnerabilities in your remote access infrastructure. Engage a qualified security consultant to conduct these assessments and provide recommendations for improving your security posture. Address any identified vulnerabilities promptly.
Establish a business continuity plan that includes procedures for maintaining remote access capabilities in the event of a disaster or outage. Ensure that you have redundant systems and backup plans in place to minimize disruption to your business operations. Regularly test your business continuity plan to ensure that it is effective.
Continuously monitor the remote access landscape for new threats and vulnerabilities. Stay informed about the latest security best practices and implement them promptly. Adapt your security measures to address emerging threats and protect your remote access infrastructure.
The world of remote access is constantly evolving, with new technologies and solutions emerging regularly. By staying informed, implementing best practices, and adapting to the changing landscape, you can leverage the power of remote access to enhance your productivity, collaboration, and security.
Remember to always prioritize security when using remote access software. Never share your credentials with anyone and be wary of suspicious requests for remote access. Keep your software up to date and use strong, unique passwords for all of your accounts. By following these simple precautions, you can help protect yourself from cyber threats.
Ultimately, the best remote access solution is the one that best fits your individual needs and requirements. Take the time to research the various options available and choose the solution that is right for you. With the right remote access software, you can stay connected and productive from anywhere in the world.
Consider the scalability of the remote access solution. As your business grows, you may need to add more users or devices. Choose a solution that can easily scale to accommodate your growing needs. Some solutions offer flexible licensing options that allow you to add or remove users as needed.
Look for remote access solutions that offer robust reporting and analytics capabilities. These features can provide valuable insights into how your remote access infrastructure is being used and help you identify potential security risks or performance bottlenecks. Reporting and analytics can also help you optimize your remote access policies and procedures.
Evaluate the integration capabilities of the remote access solution. Does it integrate with other tools and systems that you use, such as your CRM, help desk, or identity management system? Integration can streamline your workflows and improve overall efficiency.
Consider the impact of remote access on your network performance. Remote access can consume significant bandwidth, especially when streaming video or transferring large files. Choose a solution that is optimized for network performance and that minimizes the impact on other applications.
Look for remote access solutions that offer mobile device management (MDM) capabilities. MDM allows you to remotely manage and secure mobile devices that are used to access your network and data. MDM can help you enforce security policies, track device location, and remotely wipe devices if they are lost or stolen.
Evaluate the level of customization offered by the remote access solution. Can you customize the user interface, branding, and settings to match your organization's needs? Customization can help you create a more seamless and user-friendly experience for your employees.
Consider the regulatory requirements that apply to your industry. Some industries have specific regulations regarding data privacy, security, and compliance. Choose a remote access solution that meets these regulatory requirements.
Look for remote access solutions that offer multi-factor authentication (MFA). MFA adds an extra layer of security by requiring users to provide multiple forms of authentication, such as a password and a code from their mobile device. MFA can help protect against unauthorized access to your network and data.
Evaluate the remote access solution's vulnerability management capabilities. Does the solution provide tools for identifying and remediating vulnerabilities in your remote access infrastructure? Vulnerability management can help you proactively address security risks and prevent attacks.
Consider the long-term cost of ownership of the remote access solution. In addition to the initial purchase price, factor in ongoing costs such as maintenance, support, and upgrades. Choose a solution that offers a good balance of features, performance, and cost.
- Exklusive Einblicke Indische Influencer Dramen Mehr Jetzt Entdecken
- Autumn Renae Bio Onlyfans More Discover Now
Arduino IoT Cloud Remote Control for Your Maker Projects Tom's Hardware
RemoteIoT Monitor Software Free The Ultimate Guide For Remote Monitoring

Free RemoteIoT Management Software Empowering Businesses With Advanced